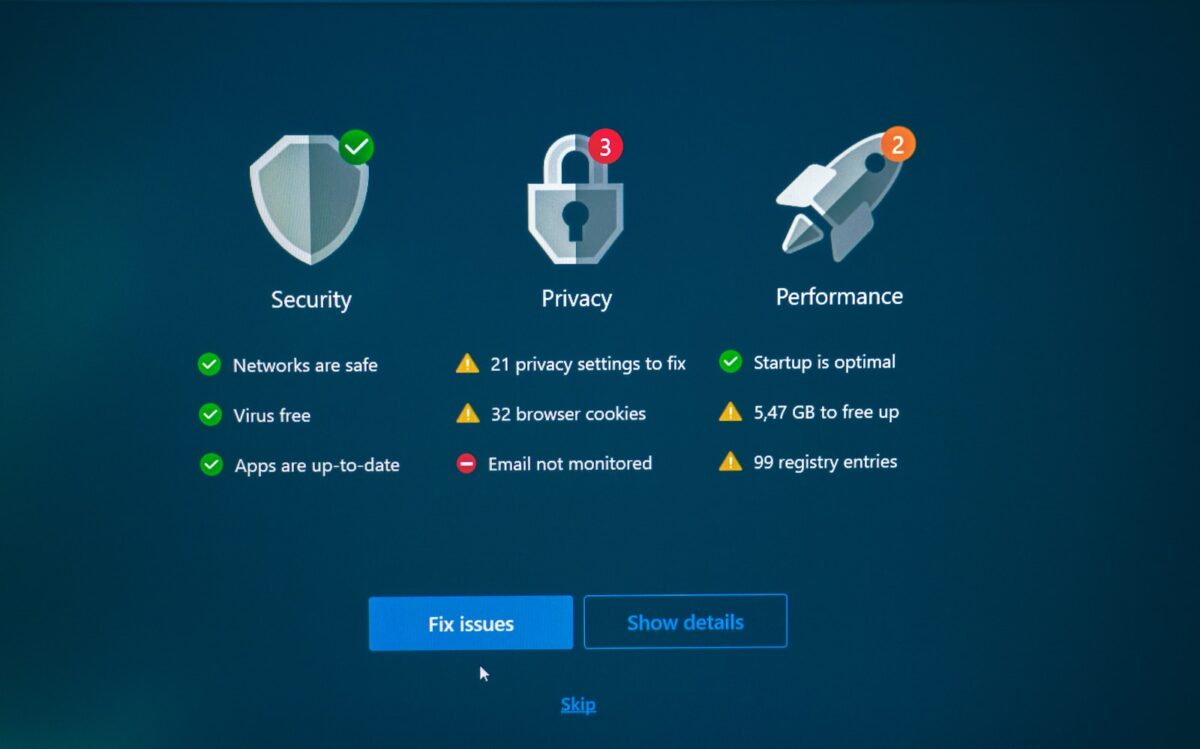
Performance optimization – operational efficiency improvement
Maximizing throughput hinges on precise adjustments to resource allocation and process speed. By recalibrating workload distribution and minimizing idle cycles, companies have reported up to a 30% surge in production rates within six months. Leveraging advanced monitoring tools enables real-time tracking of bottlenecks, directly translating into faster cycle times without additional capital expenditure. Targeted refinement … Read more