Angel investing – individual crypto project backing
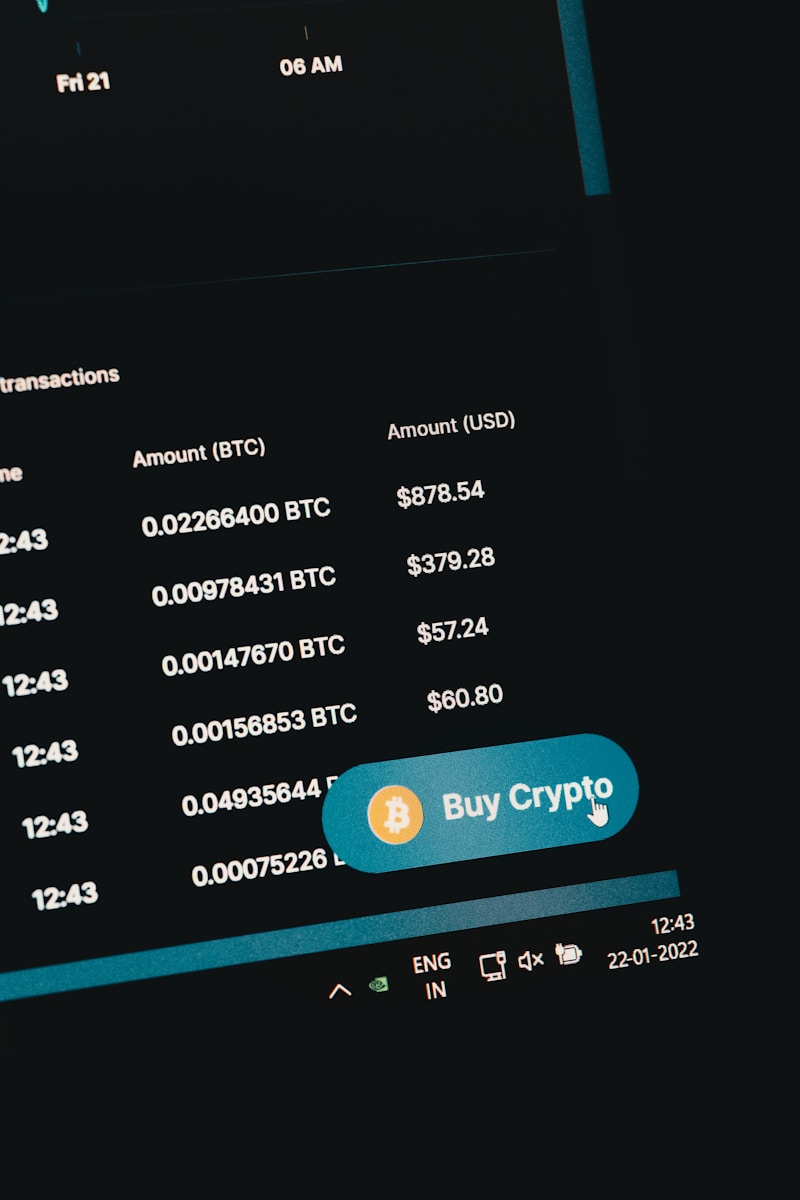
Seed funding from private benefactors remains a critical driver for emerging blockchain ventures. Personal capital injections at the earliest stages can accelerate development cycles, offering startups the financial runway necessary to refine protocols and expand user adoption before institutional financing becomes accessible. Data from recent market reports indicates that approximately 40% of successful decentralized applications … Read more